


Key & certificate management built for humans & agents
Goodkey provides frictionless key and certificate management for humans, autonomous agents & workloads — enabling secure encryption, signing, data integrity and authentication.
Be the first in line! Sign up for early access.
Request early access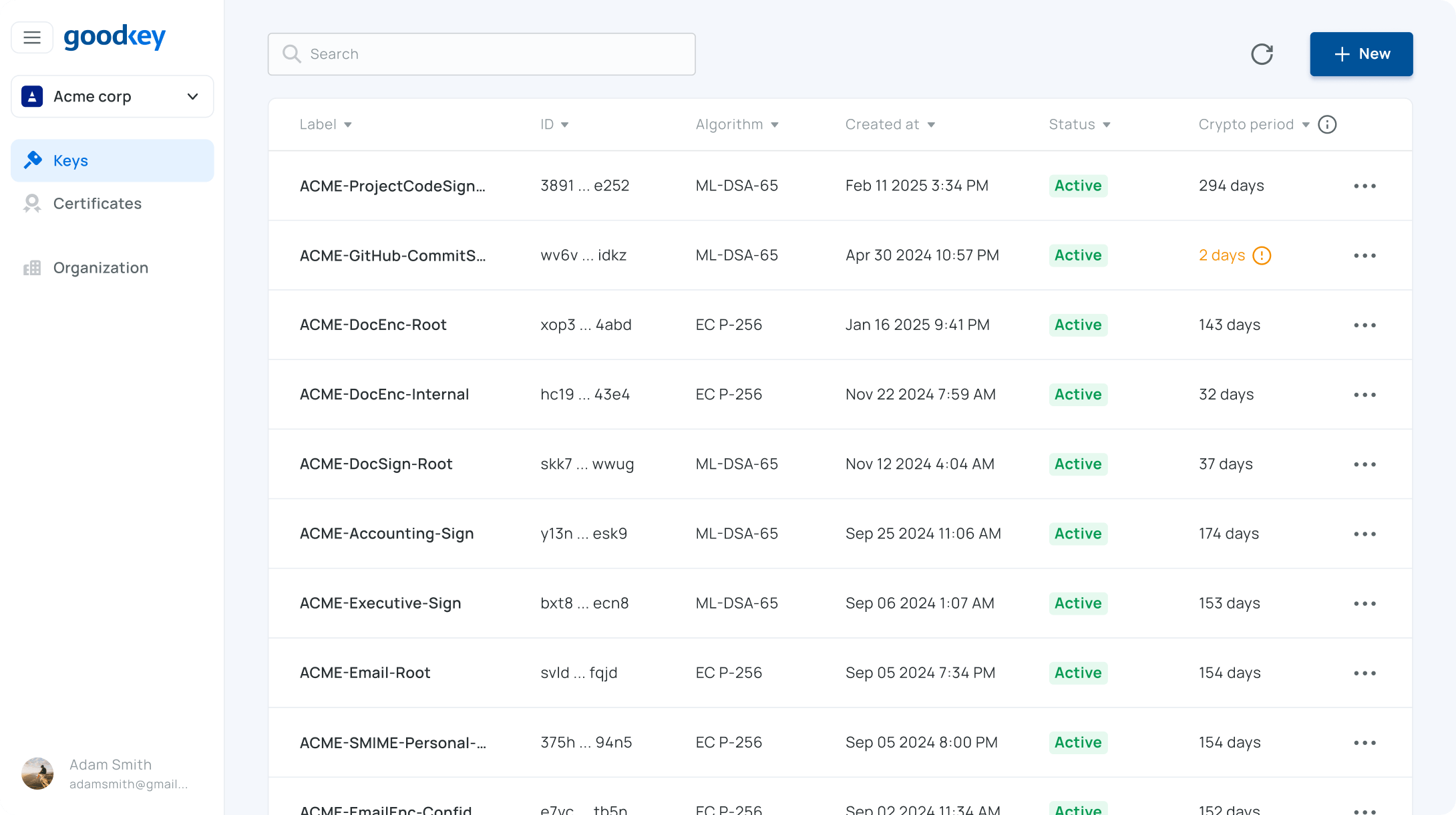
Why ineffective cryptography impacts the bottom line
the average global cost of a data breach, highlighting the significant financial impact of response activities.
Sourceof security failures will result from inadequate management of identities, access, and privileges by 2023.
Sourceof breaches stem from compromised credentials, with phishing being a major vector for credential theft.
SourceEmpowering teams with modern cryptographic workflows
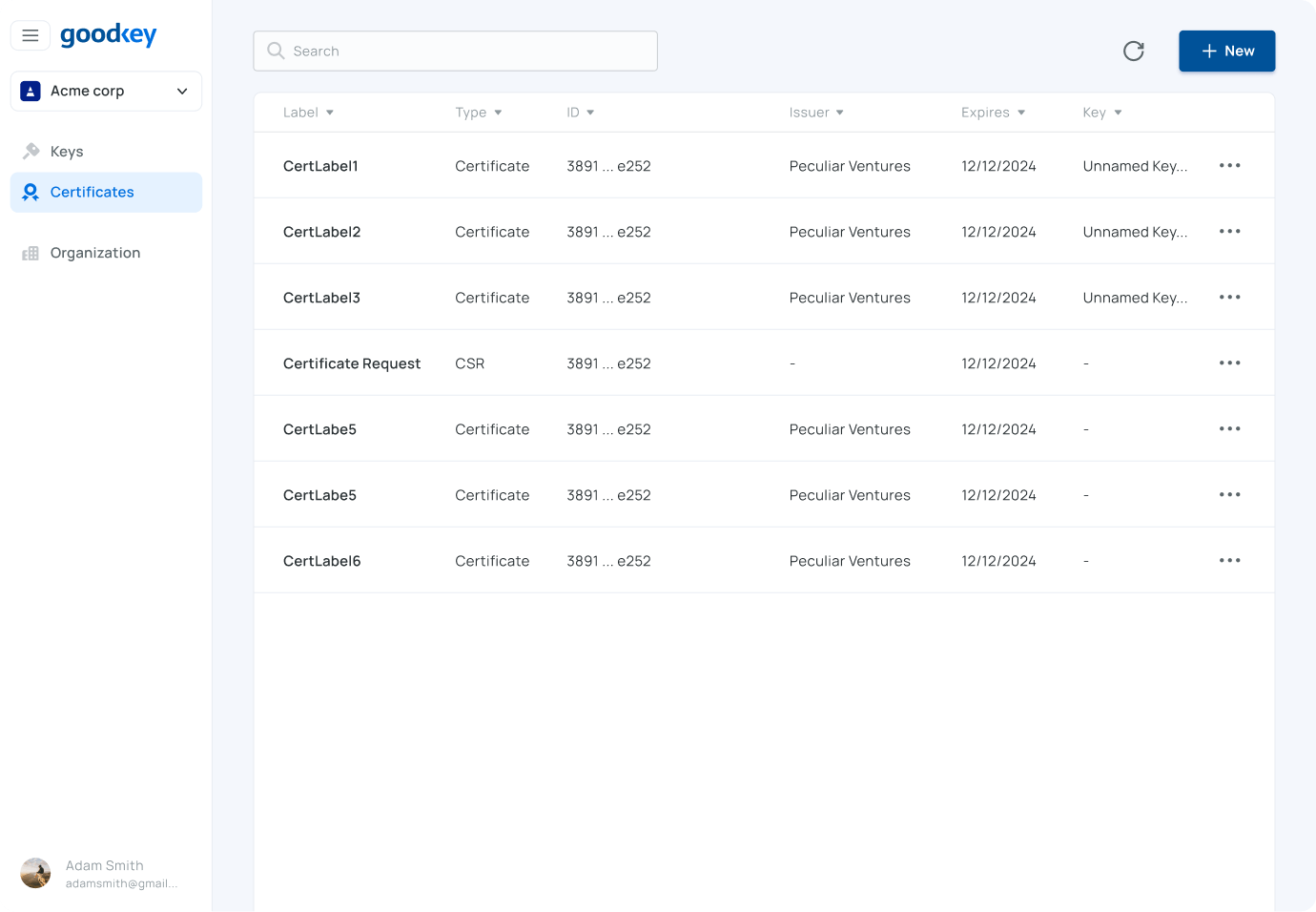
Goodkey simplifies the enrollment and lifecycle management of code signing certificates and keys. We support classical algorithms (RSA, ECC) and post-quantum cryptography (ML-DSA, SLH-DSA), with automated workflows that enhance visibility and security— without slowing down developers or deployments.
Seamlessly integrates into CI/CD pipelines for automated, continuous signing. Ensures model, build, and container integrity by preventing unauthorized changes.
Supports quorum approvals (e.g., 2-of-3) for secure decision-making. Provides temporary, time-limited SSH, RDP and MTLS credentials to reduce standing risk.
Centralized dashboard for issuing, renewing, and managing keys and certificates. Tracks every operation with detailed audit logs to support compliance and incident response.
Empower your organization with seamless, reliable, and user-friendly cryptographic management.
Local client
Your cryptographic gateway integrating with existing systems through PKCS#11, with native Windows and macOS support. Enables secure signing and encryption operations.
Local client
Signing
Encryption
API
Web client
Key Management
Audit
HSM
Empowering developers to build, not manage
Automate credential deployment to Git, CI/CD, and SSH. Provides certificates and keys management without fragmented tools.
Just-in-time access.
Automated signing.
Custom integrations with API-first design.
Less time managing. More time building.
Making Gmail privacy simple & secure
Goodkey encrypts emails on your device, ensuring only intended recipients can access them. It integrates with Gmail seamlessly and simplifies compliance with GDPR, HIPAA, and CCPA.

Building trust in AI-generated content
Automates signing workflows for AI-generated content, includes cryptographically verifiable origins, and streamlines team-based approvals. With compliance-ready tools, it helps scale authenticity standards seamlessly.
Streamlined approvals & collaboration, all in one place
Approve signing requests or certificate renewals via a quick message.
Grant temporary credentials to contractors or rotating staff; auto-revoke to reduce risk.
Flexible approval routing ensures quick action without delays.
Every action is logged, giving you bulletproof compliance evidence.
Are you post-quantum ready?
Government mandates for post-quantum migration are here. Goodkey helps you stay ahead with:
Seamless support for ML-KEM (FIPS 203)
Seamless support for ML-DSA (FIPS 204)
Seamless support for SLH-DSA (FIPS 205)
Support for IETF LAMPS X.509 PQC certificates
Prepare today, secure tomorrow.

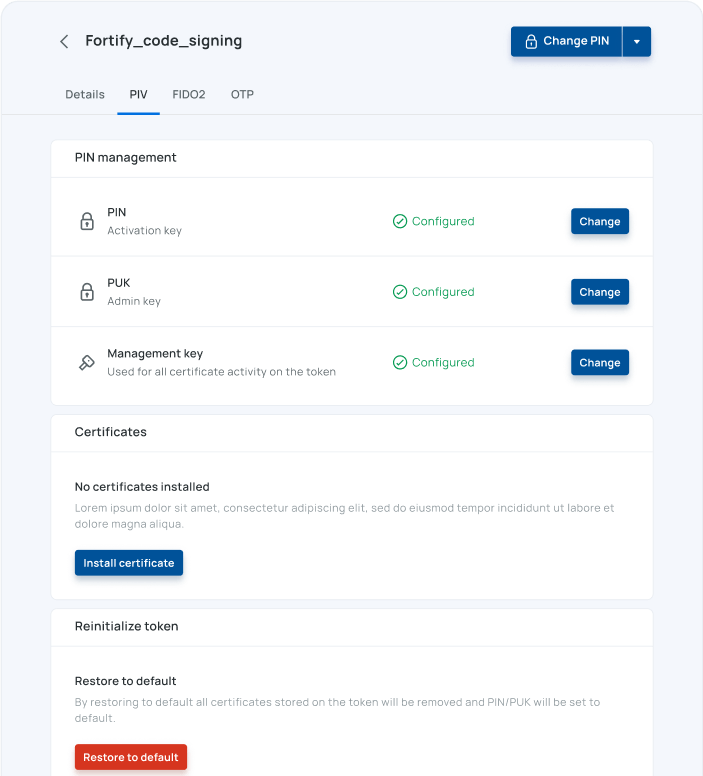
Complete authenticator management
Goodkey's device inventory empowers organizations to take full control of their authenticator deployments.
Automated discovery and model detection.
Real-time lifecycle visibility.
Automated per-device secret rotation and management.
Comprehensive audit trails.
Automated provisioning and decommissioning.
Certificate and key renewal automation.
Secure decommissioning and replacement.
From frustration to empowerment — what Goodkey delivers
- Manual processes create security gaps
- Certificate expirations cause outages
- Timely certificate management, preventing downtime
- No visibility for audits & compliance
- Content authenticity unverifiable
- Emails vulnerable in transit
- Centralized control and visibility with automated workflows
- Timely certificate management, preventing downtime
- Unblocked capability usage and best practices adopted
- Full audit trails of use and lifecycle make audits easier
- Automated C2PA-compliant signing for provenance
- Client-side encrypted emails protect sensitive communications



Get started with human & agent centered key management
Frictionless key and certificate management for humans, autonomous agents, and workloads—enabling encryption, signing, and data integrity so you can collaborate securely without compromise.
Be the first in line! Sign up for early access.
Request early access